How to generate credentials in GCP?
To access GCP, you generate credentials using Service accounts on IAM console.
The credentials in GCP include ONE single file in JSON format that contains all the neccessary information for authentication.
Project and billing
The services in Google Cloud are organized in projects, each project has its own ID, billing account and permissions to use the GCP resources through service accounts.
INFO
Each project used to deploy resources has to have a billing account with a credit card attached.
- First go to the "Create a project" console after logging in
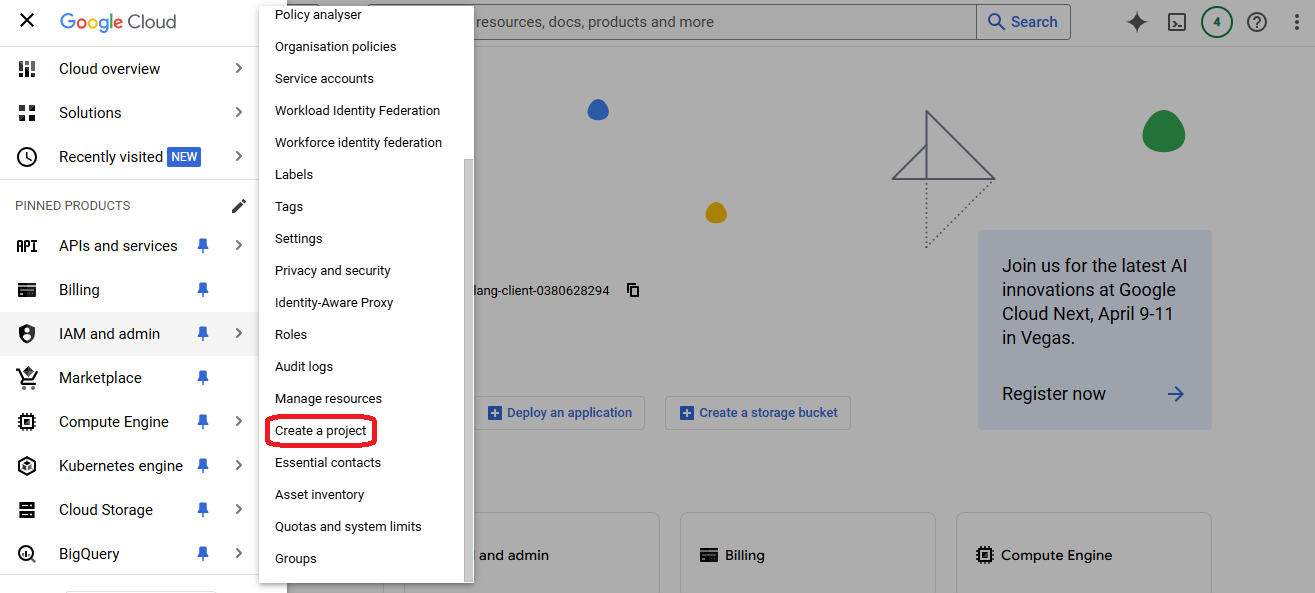
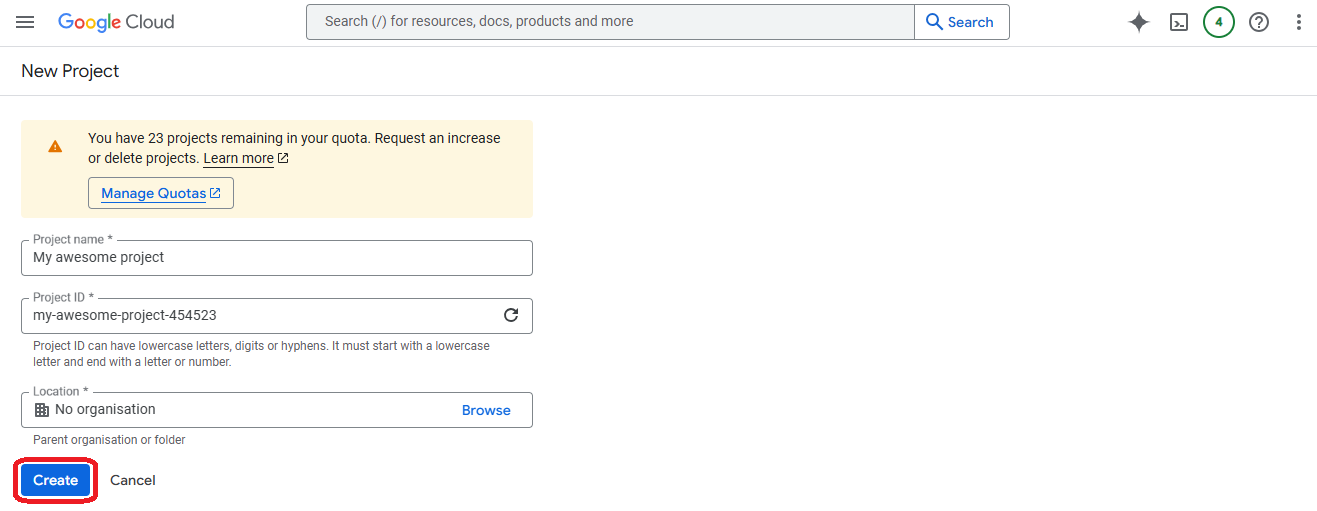
- Choose a project name and a unique project ID (to use it on CloudStudio)
- Go to "Billing" on the new created project
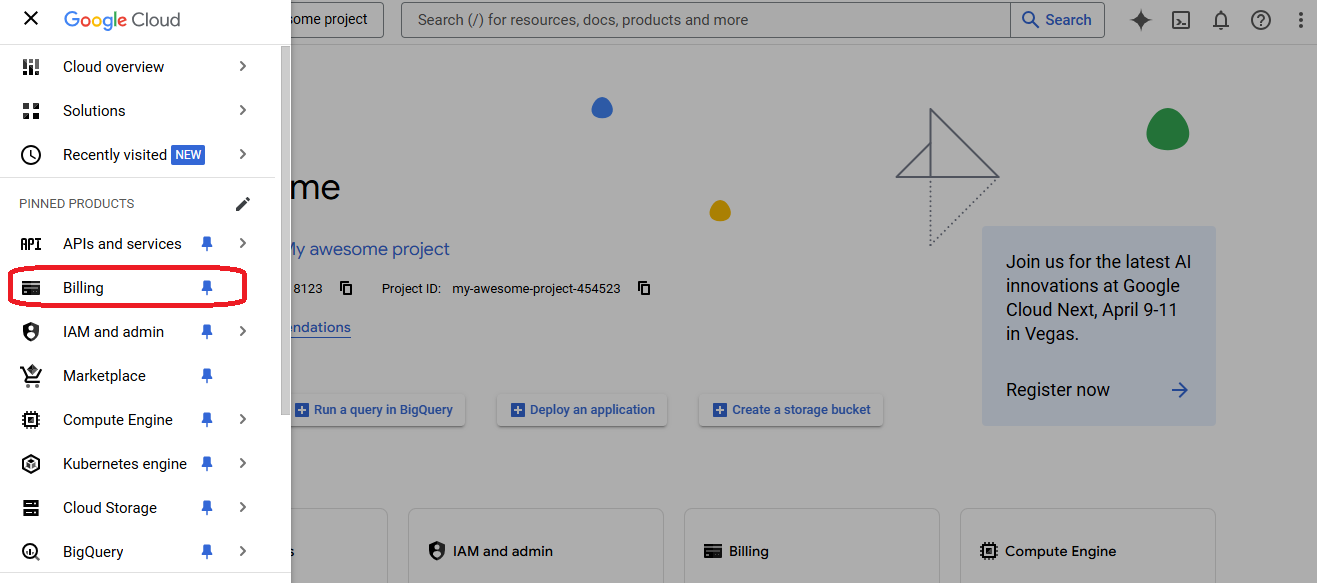
- Go to "Manage billing accounts" to create a new account
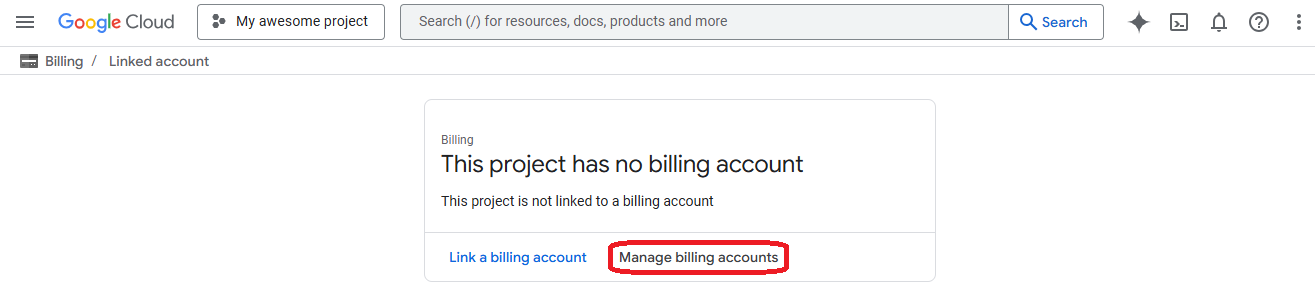
- Click on "Create account"
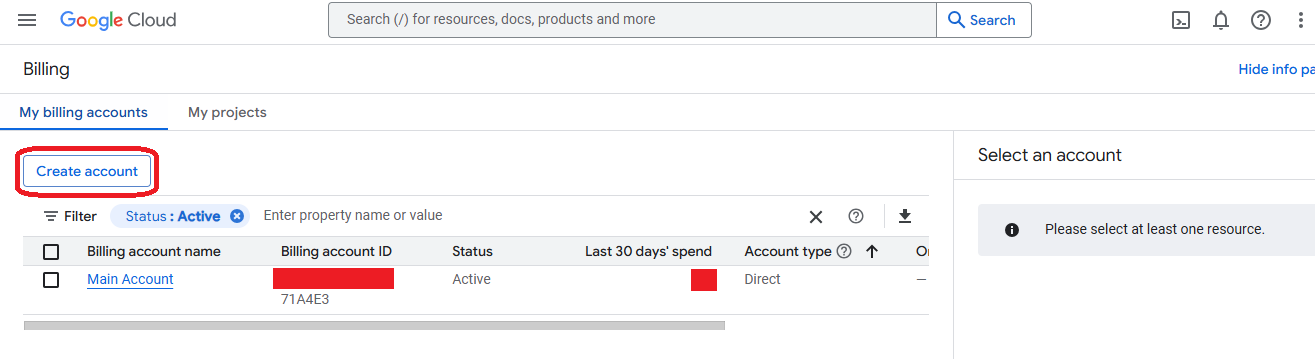
- Choose a name and a country for the new account and click on "Continue"
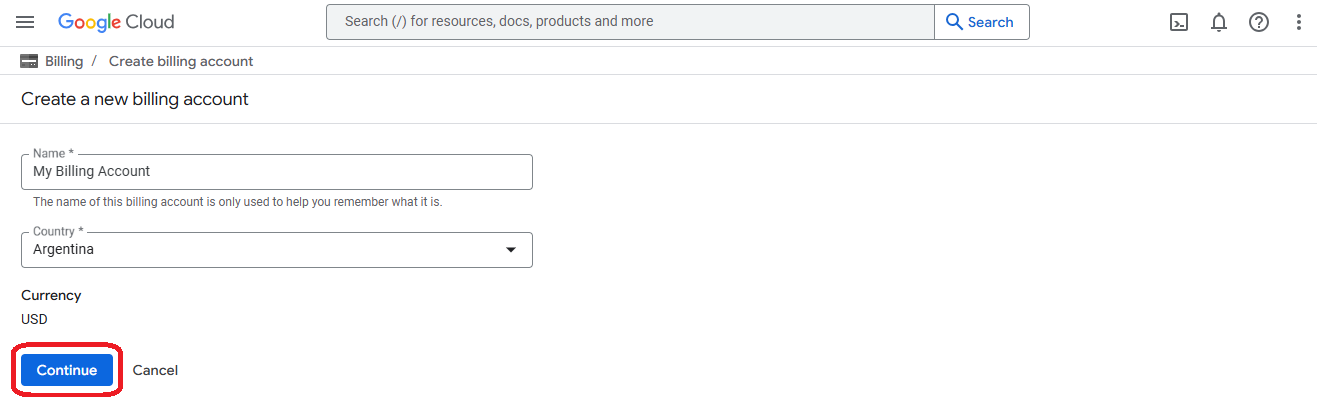
- Add or choose a credit card and click on "Submit and enable billing"
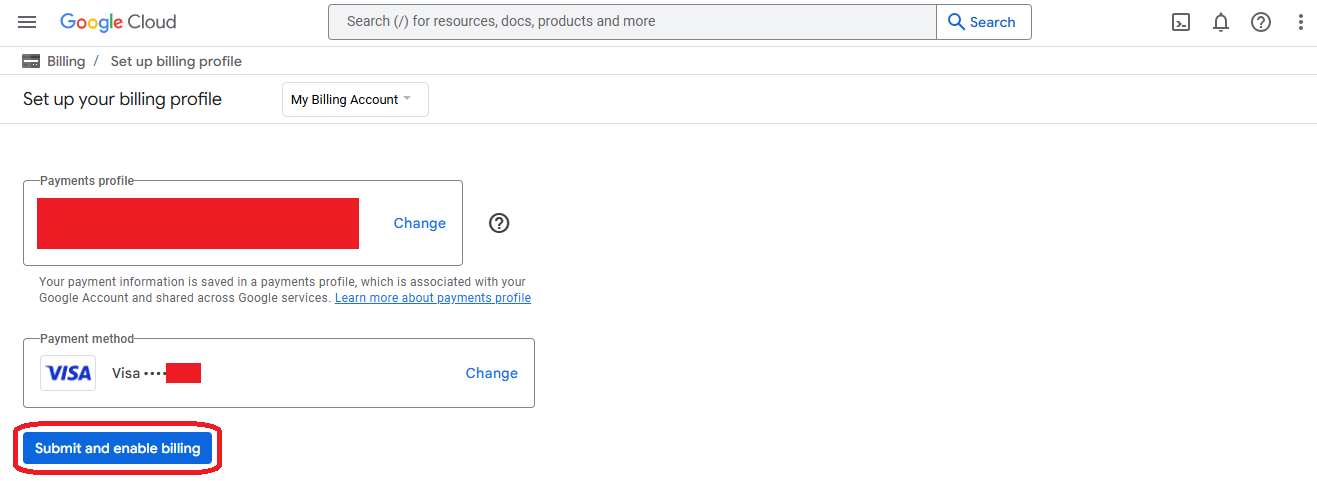
- Create a budget alert on the new billing account and go back to "billing"
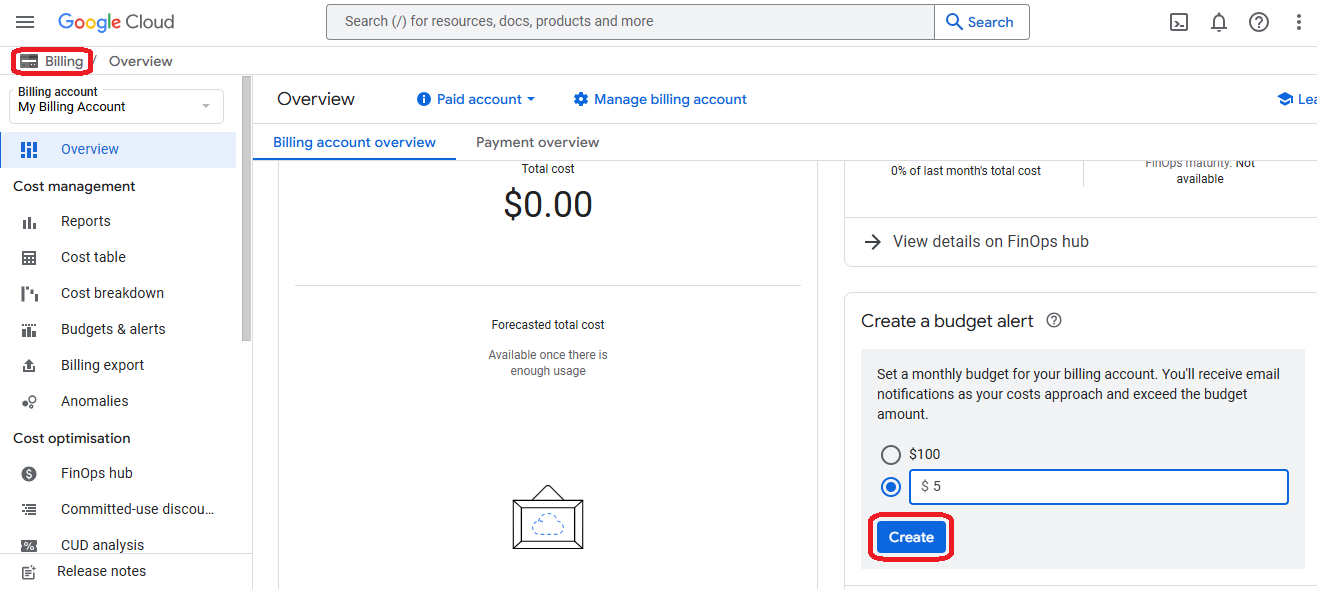
- On the tab of "My projects" select the "Change billing" action on the new project
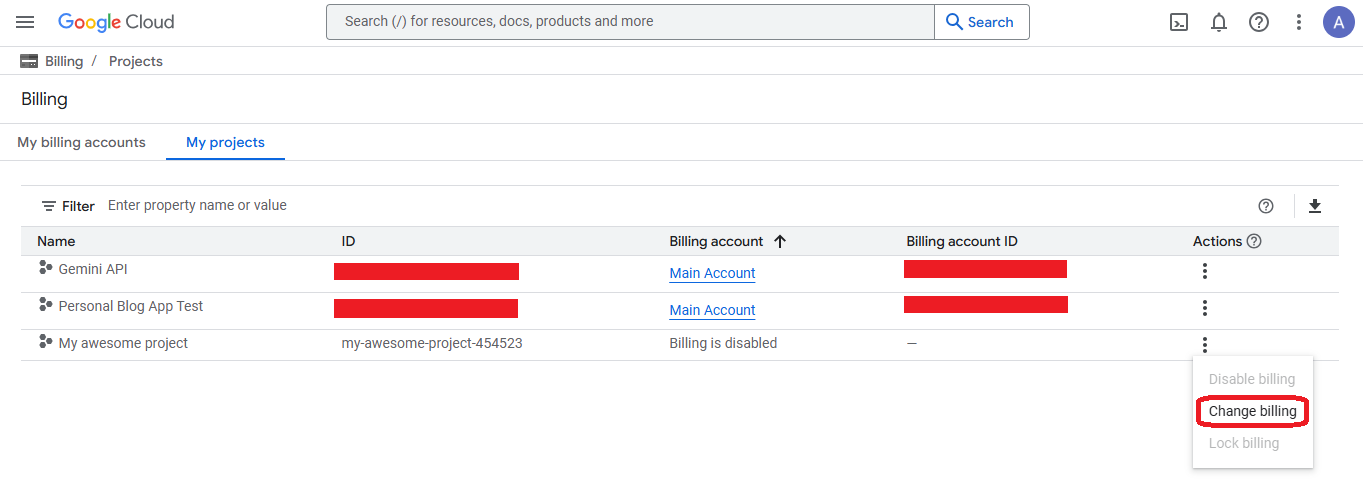
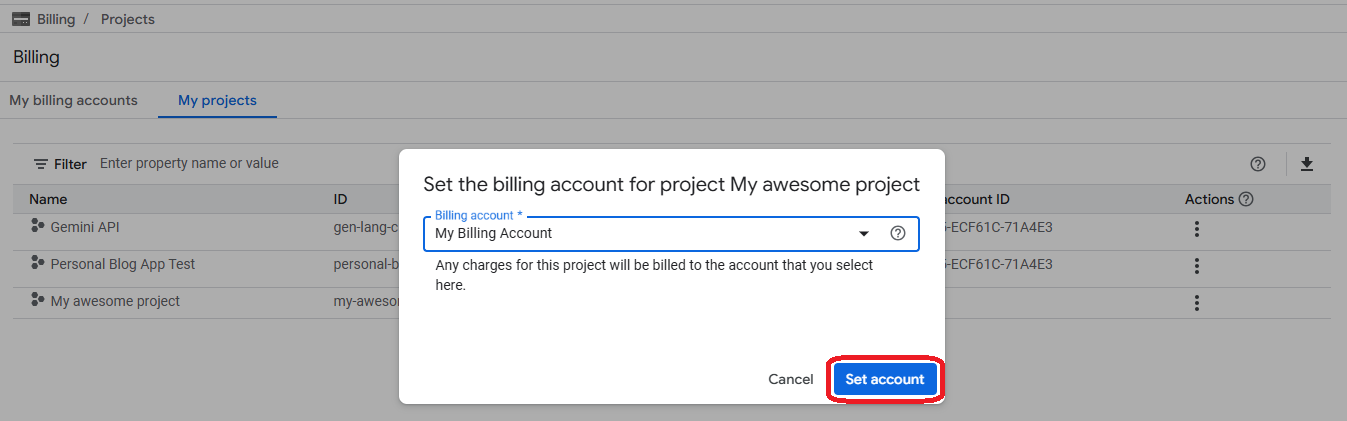
- Select the new account and click on "Set account"
Service account keys
The service accounts are used for external applications (like CloudStudio) to access resources on a GCP account, controling its access through roles and permissions.
INFO
Every service account belongs to an specific project within GCP, so every resource created though a service account will live on that specfic project. To use a service account, the external app will connect to it by a JSON file created in the IAM console and downloaded on local machine.
- First go to the "Security accounts" on the new project dashboard
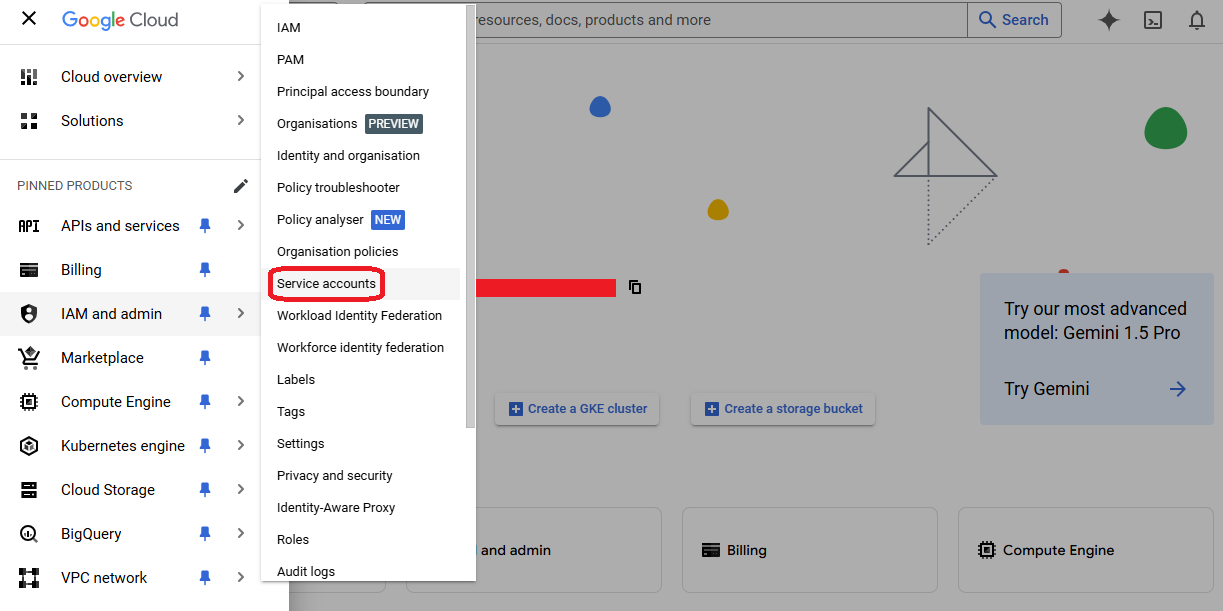
- In the new opened console click "Create Service Account"
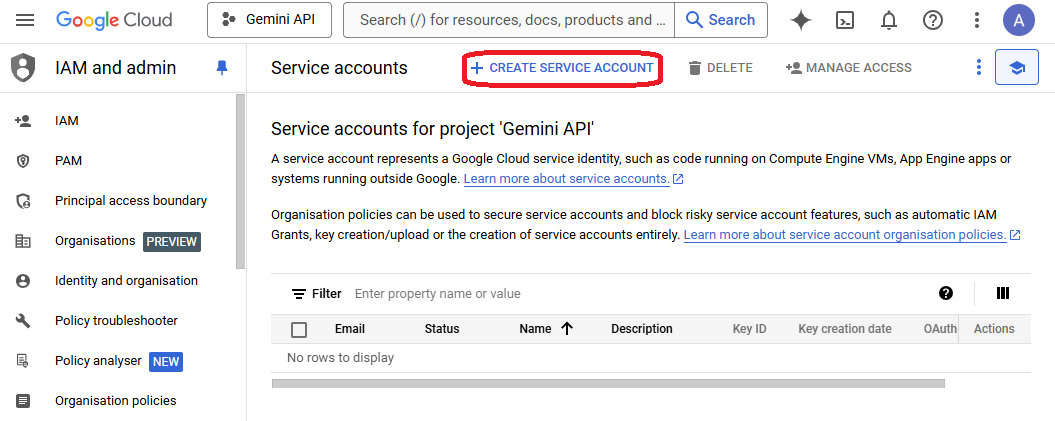
- Give it a name and appropriate description
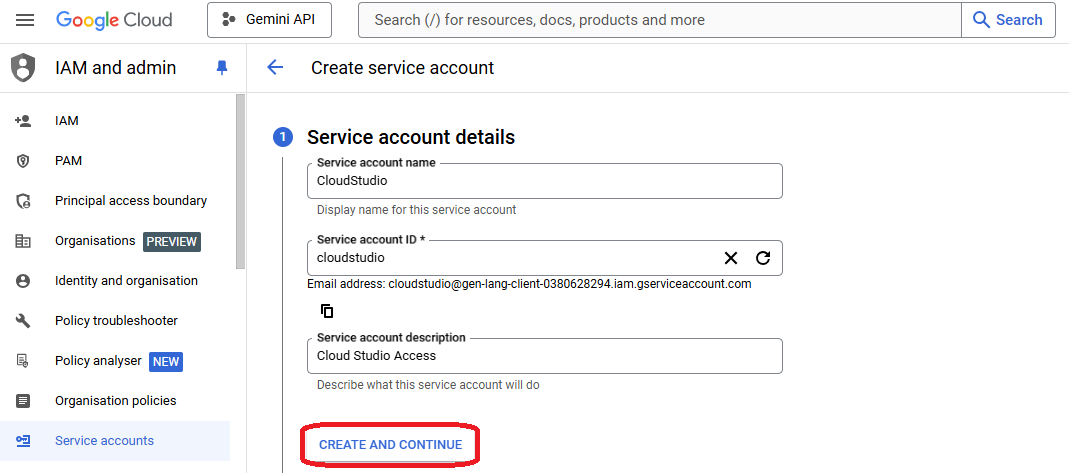
- Grant "Owner" role to access most GCP resources within that project
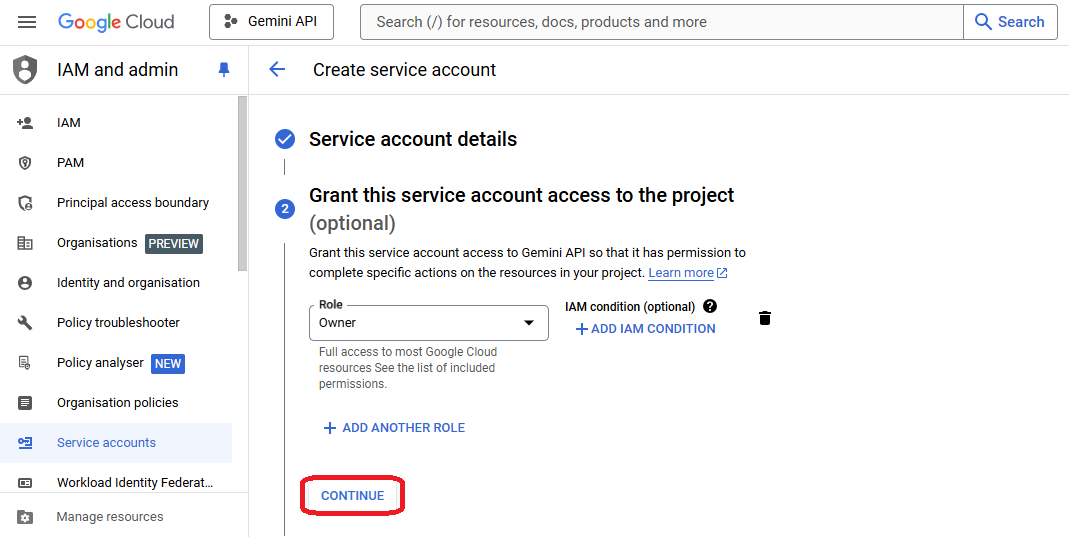
- Skip the "Grant users access" step and confirm operation
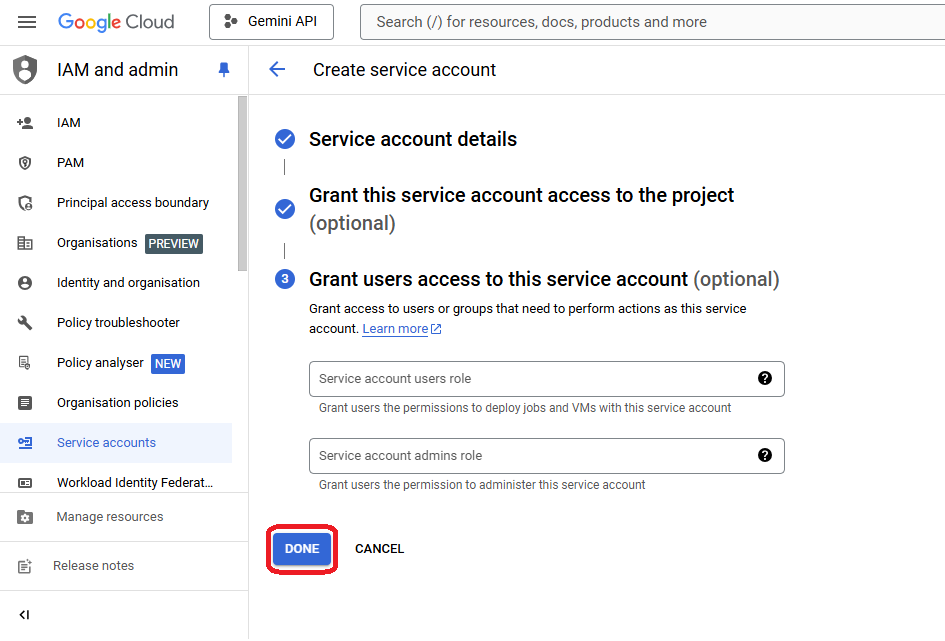
- Back to the Service accounts list, select the recently created and click "Manage Keys"
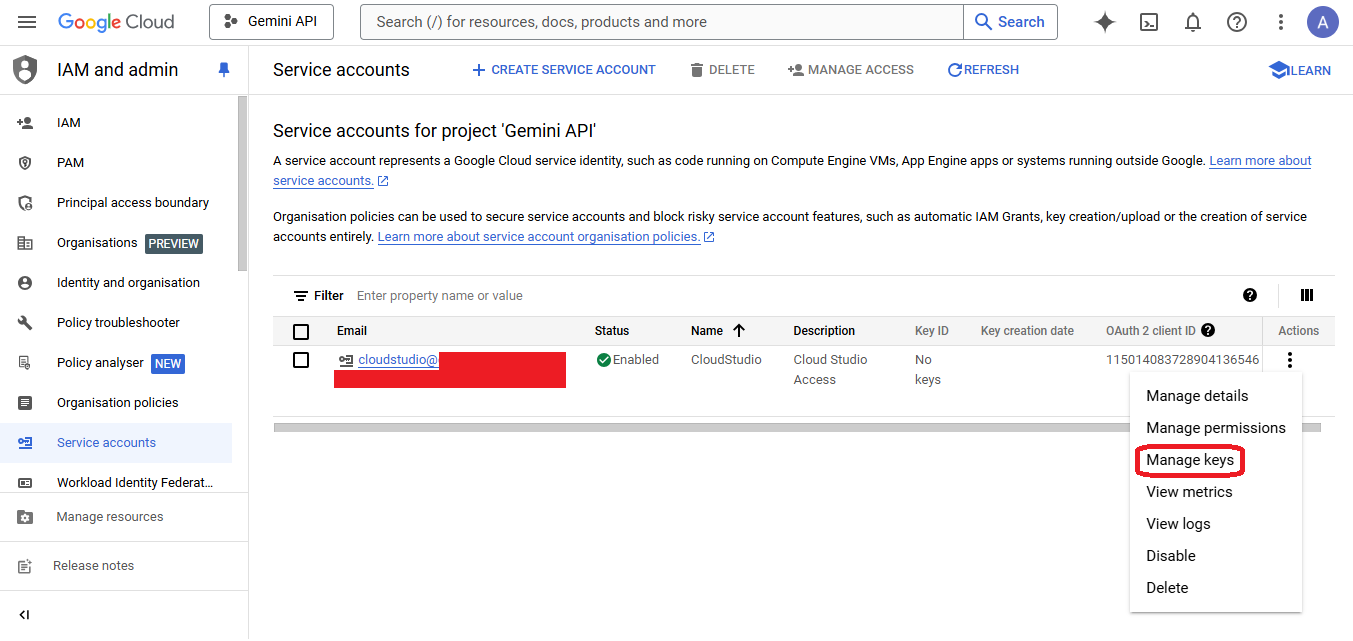
- Click on the selector "Add Key" and then on the "Create New Key" option
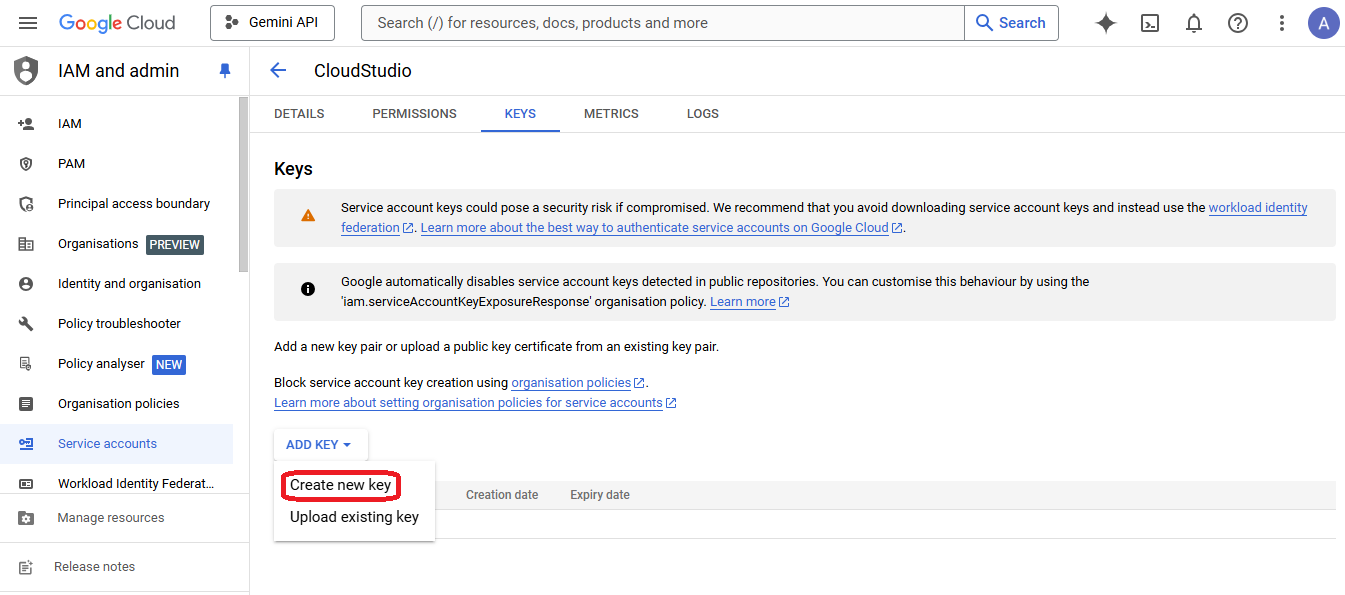
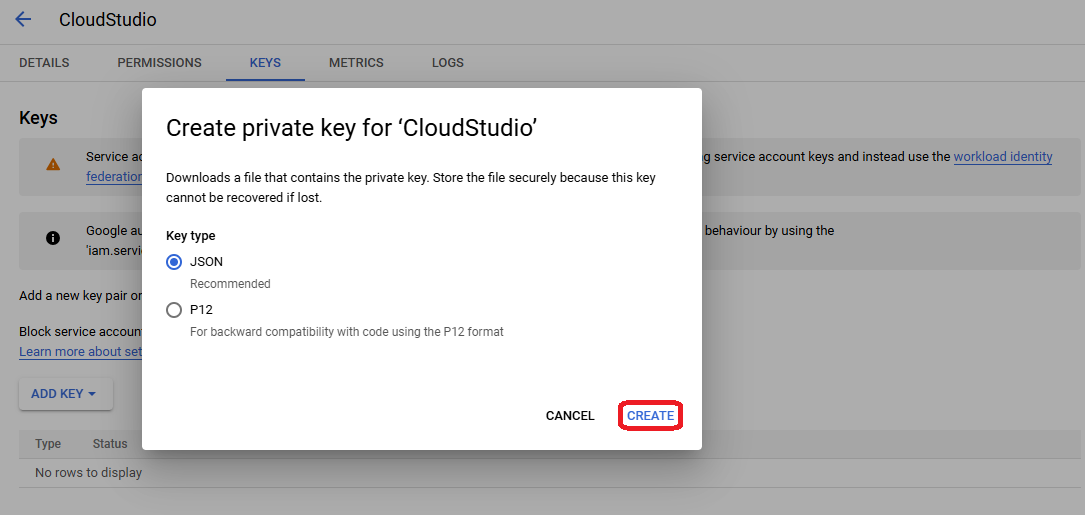
- Choose JSON format and click on "Create" to download the credentials file
APIs and Project permissions
Before start working with the new credentials, the APIs of each service to be deployed have to be enabled on the project.
INFO
The APIs for each Google service of a project can be enable or disable on the library.
- Go to "library" in the APIs and services section
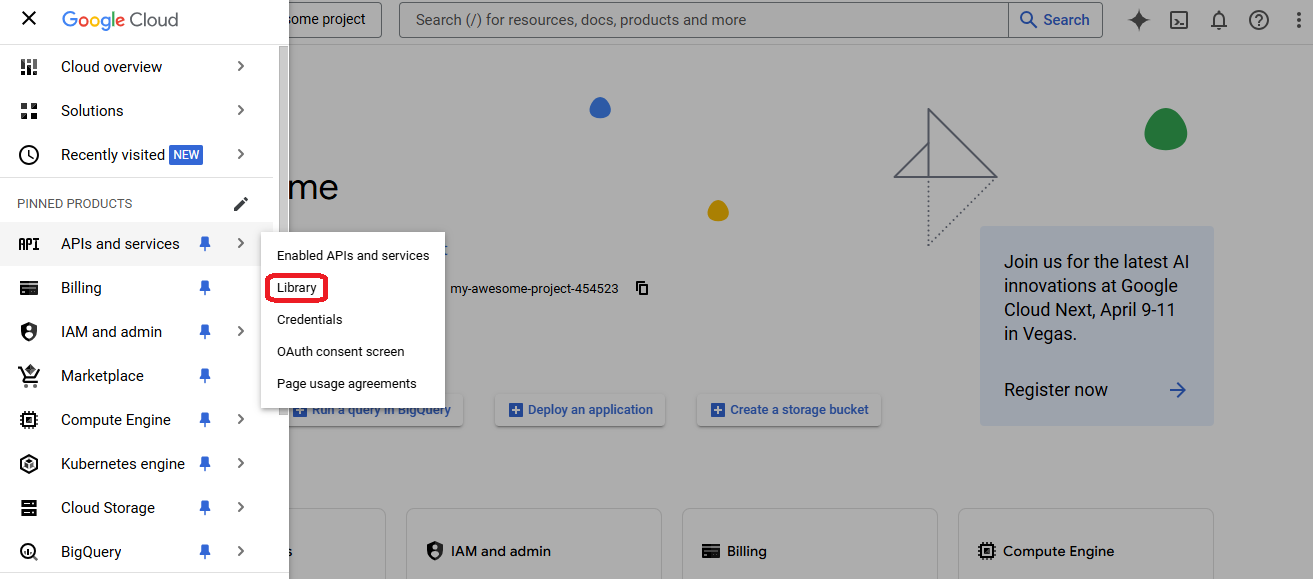
- Search for the service you want to deploy on Google cloud
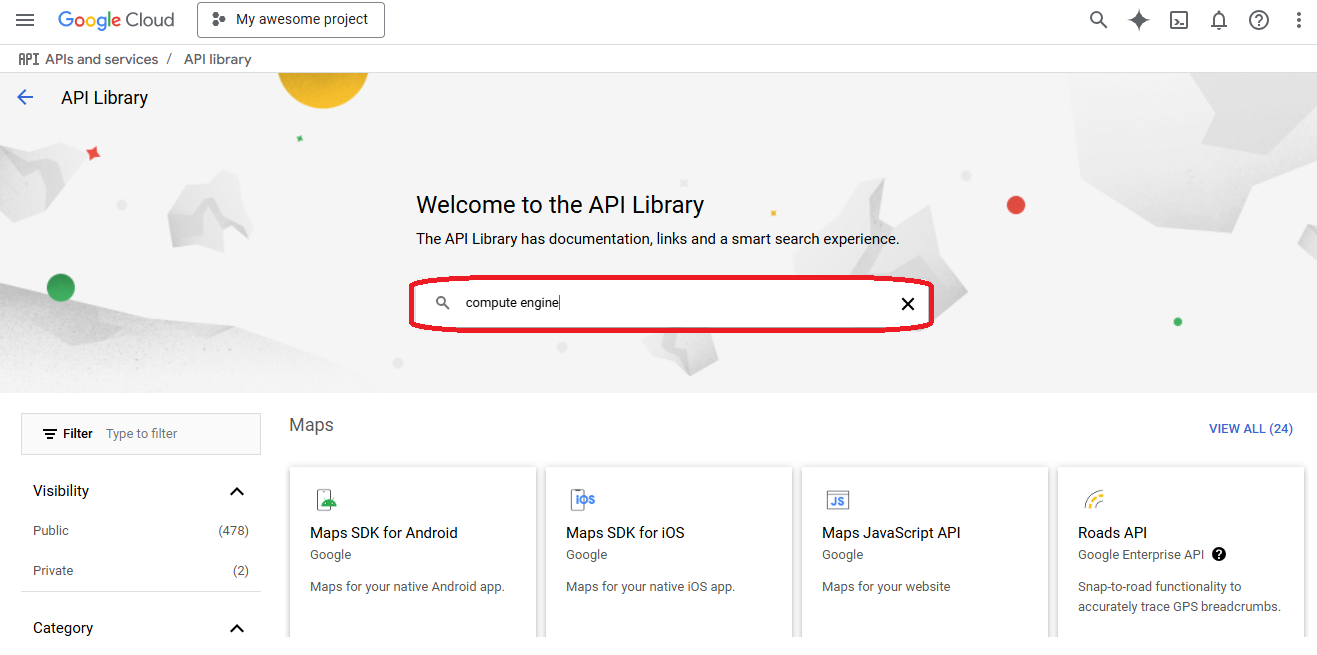
- Select the service you are looking for
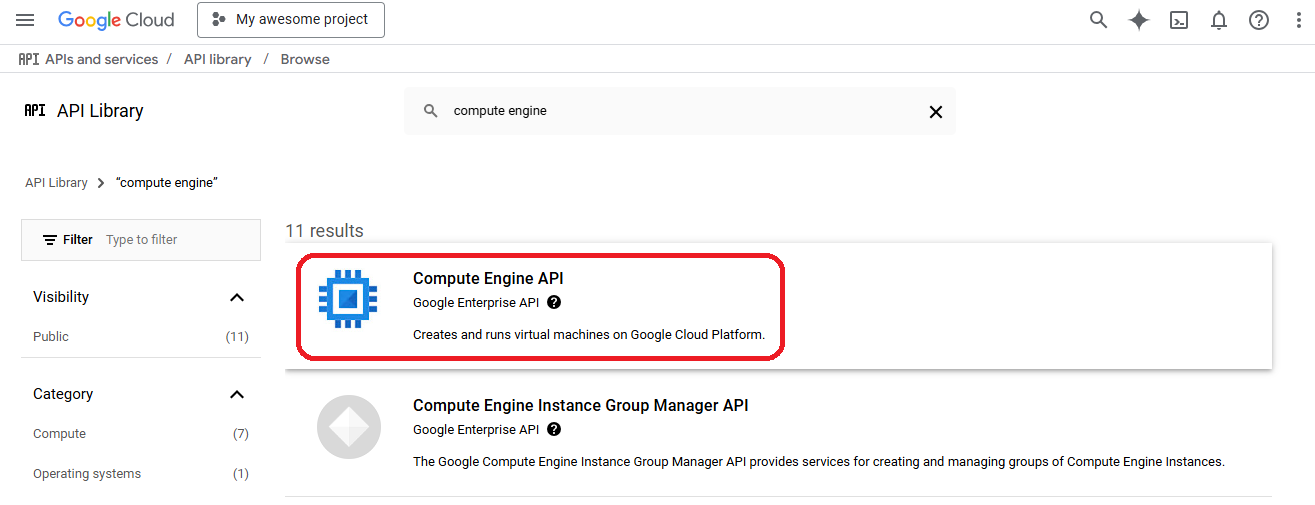
- Click on "enable" and wait until it takes effect
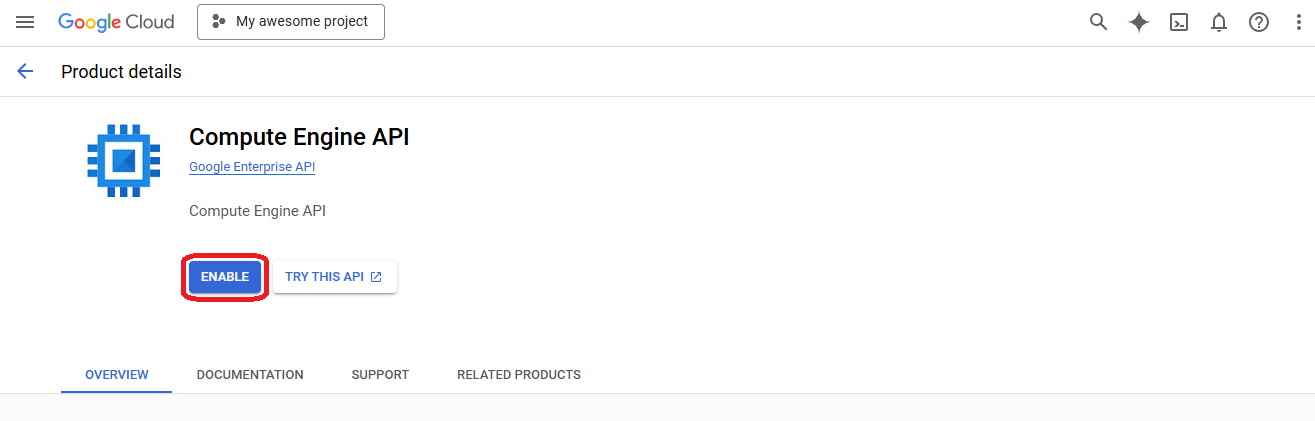
INFO
Additionally if you want to use the credentials generated on "Project A" to deploy resources on "Project B" you'll need to add the same service account with owner role to "Project B".
- Go to "IAM" console on the "Project B" you want to link to the credentials of "Project A"
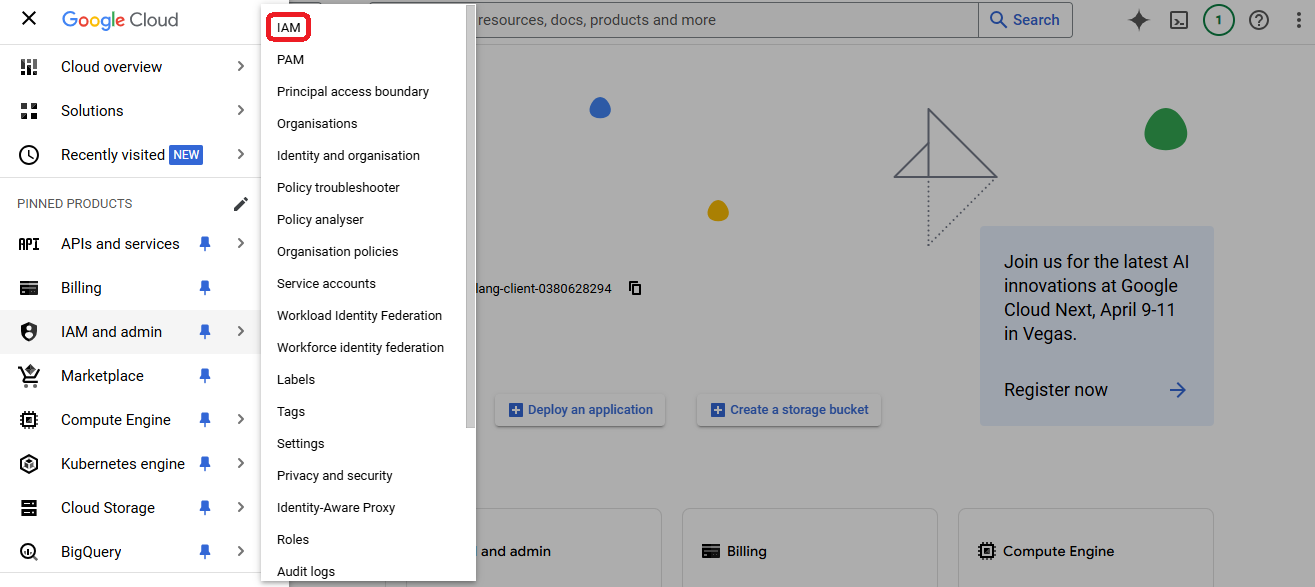
- Click on "Grant access"
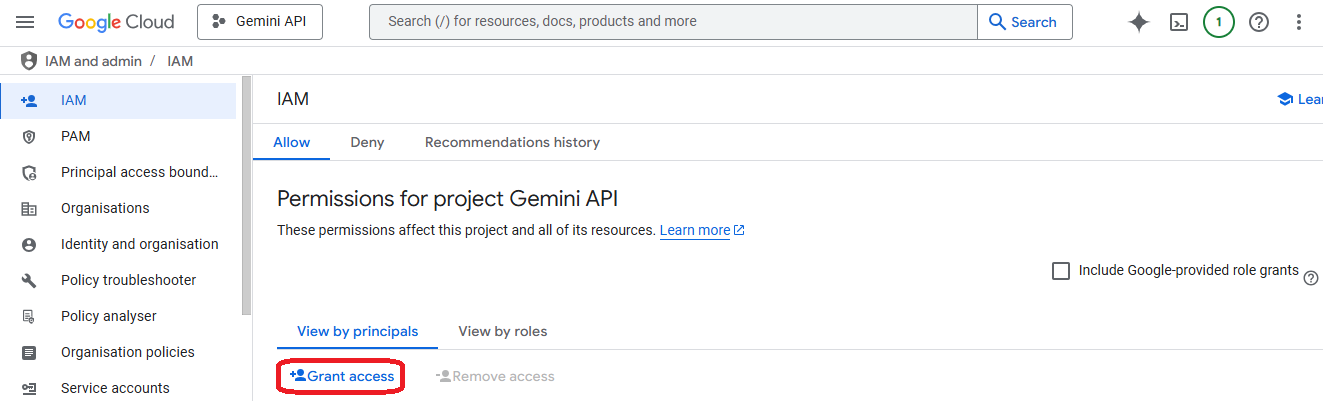
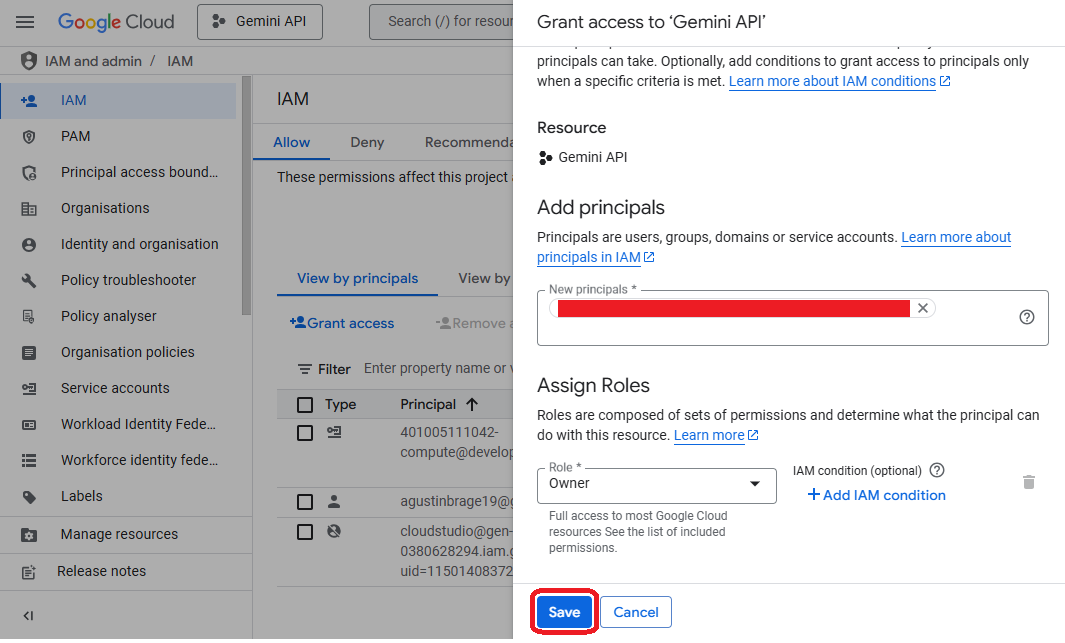
- Select the name of the service account of "Project A" and give it an owner role, save it
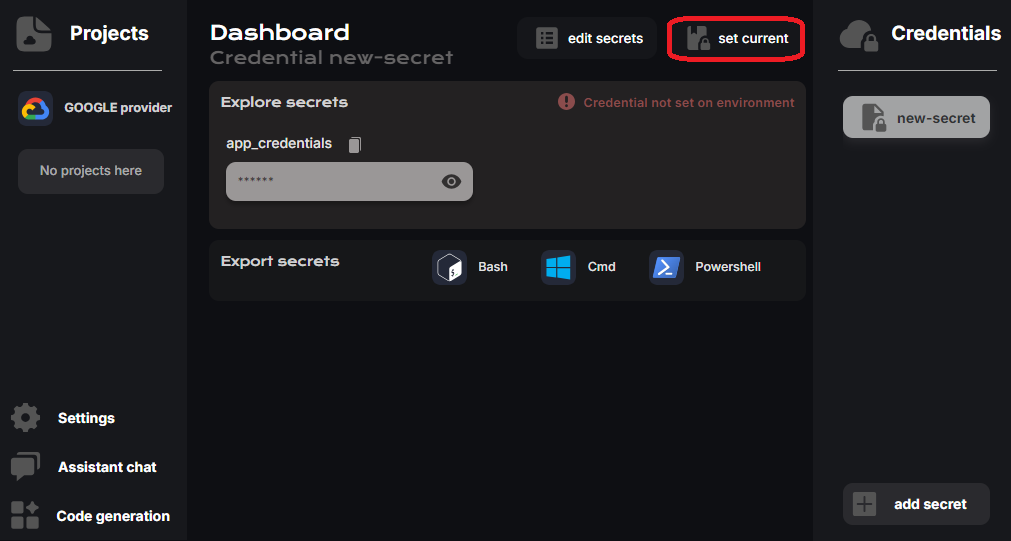
Add secrets to CloudStudio
INFO
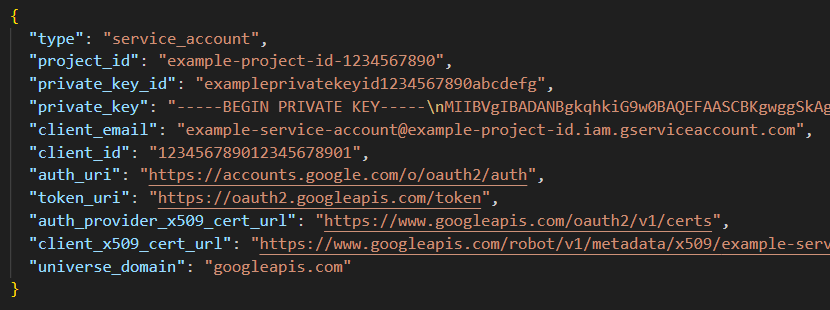
After downloading the credentials JSON file, its content should look like this
- Go to the Google provider on the CloudStudio dashboard and click "add secret"
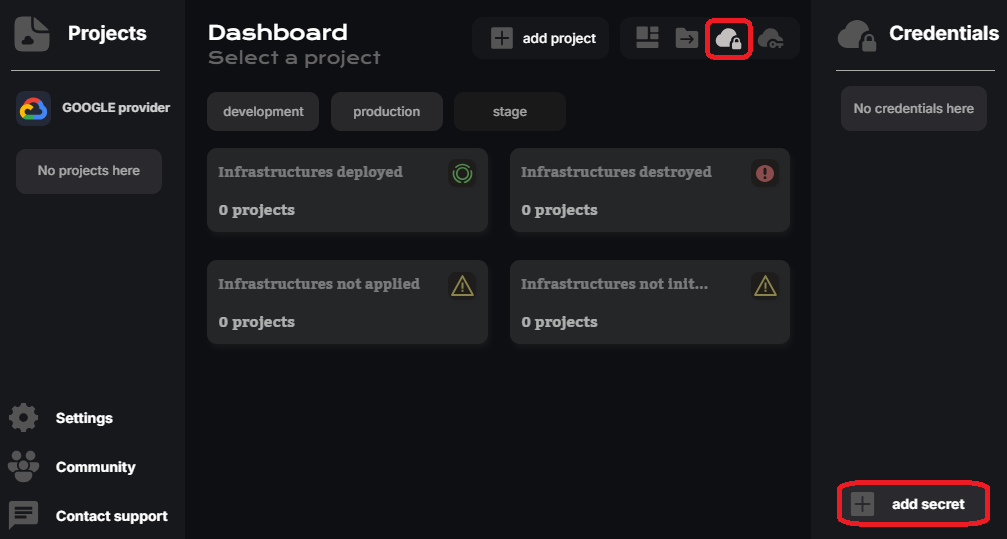
- Copy the root to the JSON file, paste it on the app_credentials value and apply changes
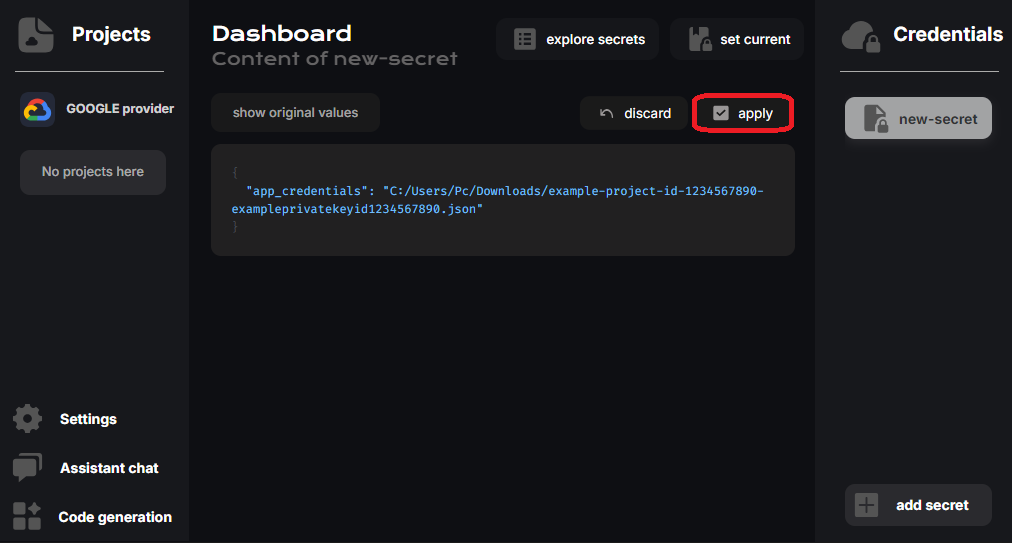
- Finally set created secret to the current app environment